Manual intrusion testing, black box testing, test first and pay later
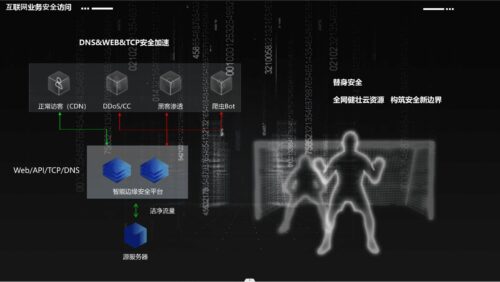
WEB security acceleration
Web/API one-stop security acceleration service, IPv4/IPv6 dual-stack adaptation, empowering enterprises' digital transformation and protecting digital business.
Business-level Web Application Firewall
Intrusion prevention: AI+semantics+intelligent rules multi-engine driven, supporting targeted threat trapping
Content security: website snapshots, content tamper-proofing, multiple large-scale network security without any hacking
Business security: Bot risk management, intelligent human-machine identification, and refined access control
Dynamic acceleration of the entire site
400+ service nodes, AI intelligent routing
Global load balancing, dynamic resource expansion Global load balancing, dynamic resource expansion Shared cache, layered preheating
Unmetered DDoS Protection
30T reserve bandwidth, self-built cleaning center, full defense, cost controllable, experts respond in real time, online actual combat
TCP Security Acceleration
One-stop secure acceleration service for TCP services, suitable for native client scenarios such as games and smart terminals
Performance & Acceleration
400+ node resources worldwide, back-to-source load balancing, dynamic routing optimization, transmission protocol optimization, global acceleration
Unmetered DDoS Protection
30T reserve bandwidth, self-built cleaning center
Precise access control, supporting customized defense strategies
Security Acceleration SDK
Based on the zero-trust security concept, we build an integrated end-edge-cloud in-depth security acceleration to solve various security issues faced by PC clients, mobile, and new IoT scenarios.
Equipment risk identification
Accurately identify debugging/injection/Hook/DUMP, device tampering, system root, network environment, App tampering, simulator operation, multi-opening operation, group control operation, and provide precise access control capabilities
Link encryption and trusted communication
High-intensity dynamic encryption algorithm realizes one machine one key, one chain one key, and encrypted tunnel ensures data transmission security. Hackers cannot capture packets to obtain business-related data, and cannot make any forgery or replay attack requests.
Network-wide security acceleration
Robust network infrastructure, intelligent routing, nearby network node access, UDP multi-channel transmission, global acceleration and other technologies ensure ultra-low latency and high reliability
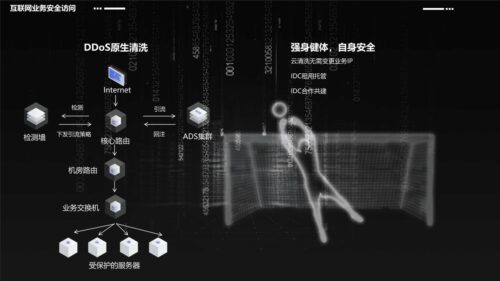
DDoS defense
Years of research on black and gray industries, attack methods, and online combat experience have created a three-level compound confrontation model. The innovative edge-cloud integrated architecture has shifted the traditional single hardware + hard resource confrontation to multi-dimensional software + elastic resource confrontation.
Bot Automated Defense
Relying on equipment risk identification and trusted communication capabilities, it can solve various security issues of the business and eliminate all unauthenticated traffic. It can protect against the following scenarios: malicious registration, database collision, brute force cracking, large-volume CC attacks on APPs, SMS/verification code interface swiping, grabbing wool/grabbing red envelopes, malicious flash sales of limited-time and limited-purchase products, malicious ticket checking/swiping, valuable information crawling, machine batch voting, flooding/malicious comments, and channel volume cheating
Intrusion prevention
Based on the zero-trust security architecture, the real host of the business is hidden, and hackers cannot launch scans and targeted intrusions on the Internet, so there is no need to worry about 0DAY/NDAY. At the same time, it is supplemented by an intelligent intrusion detection engine to mark the detected risk devices
Link security
High-intensity dynamic encryption algorithm realizes one machine, one key, one chain, one key. The encrypted tunnel ensures data transmission security. Hackers cannot capture packets to obtain domain names, URLs, APIs and other business-related content data, and cannot make any forgery or replay attack requests.
App Tamper Protection
Assign a unique identification fingerprint to each file of the APP application. Replacing any file will cause it to fail to run, preventing malicious cracking such as ad virus implantation, secondary packaging, function blocking, counterfeiting and phishing
Anti-Cheat
Common cheats rely on official applications to dynamically modify game business logic, inject malicious modules during operation, modify code logic, and modify values in memory. Through the device risk identification function, you can dynamically resist debugging, injection, Hook, device tampering, App tampering, simulator operation, multi-opening operation, group control operation and other cheats
Full network acceleration
Robust network infrastructure, intelligent routing, nearby network node access, UDP multi-channel transmission, global acceleration and other technologies ensure ultra-low latency and high reliability
Alternative DNS
SDK intelligent risk control scheduling replaces domain name resolution, no DNS required, avoiding DNS attacks and hijacking