Admittedly, Blast’s reliance on 3/5 multi-signatures to control deposit addresses has been widely criticized, but most layer2 It also relies on multi-signature to manage contracts. Previously, Optimism even used only one EOA address to control contract upgrade permissions. At a time when almost all mainstream Layer2s have security risks such as multi-signature, criticizing Blast for being unsafe is more like the technical elites "looking down" on a gold farming project.
But putting aside the question of which of the above two is better,BlockchainThe significance of existence is more to solve the problem of information opacity in social consensus/democratic governance. When advocating the supremacy of technology, we must admit that social consensus itself is more important than technology, because it is the guarantee for all Web3 The basis for the effective operation of the project. In the final analysis, technology serves social consensus. A project that cannot be recognized by most people, no matter how superior the technology is, is essentially just a gorgeous appendix.
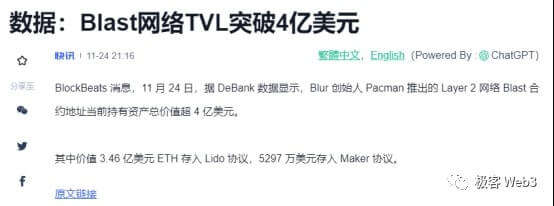
 Text: Recently, the new project Blast launched by the founder of Blur has become popular all over the Internet. This "Blast" project under the banner of Layer2资产The "Interest-earning" protocol sets a recharge address on the ETH chain. After users deposit funds into the Blast address, these funds will be used for native pledge of the ETH network and placement in MakerDAO Earn interest, etc., and the profits earned will be returned to the user.
Text: Recently, the new project Blast launched by the founder of Blur has become popular all over the Internet. This "Blast" project under the banner of Layer2资产The "Interest-earning" protocol sets a recharge address on the ETH chain. After users deposit funds into the Blast address, these funds will be used for native pledge of the ETH network and placement in MakerDAO Earn interest, etc., and the profits earned will be returned to the user.
Relying on the founder’s own halo and attractive gameplay, Blast has won theinvestment2000 million given by people美元Financing, and also attracted the participation of countless retail investors. In less than 5 days since its launch, Blast’s recharge address has attracted more than 4 million TVL美元. It is no exaggeration to say that BLast is like ManmanBear marketA strong dose of medicine instantly aroused people's enthusiasm.
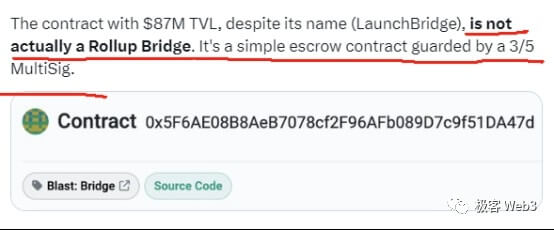
 But while Blast achieved initial success, it also attracted doubts from many experts. For example, L2BEAT and Polygon engineers both put it bluntly: the current Blast is onlyEthereumIt is just a Deposit contract that receives recharges. This contract can be upgraded under the control of 3/5 multi-signatures. In other words, the code logic of the contract may be rewritten, and you can still rug it if you want. At the same time, Blast only claims to implement the Rollup structure, but now it is just an empty shell, and even the withdrawal function will not be launched until February next year.
But while Blast achieved initial success, it also attracted doubts from many experts. For example, L2BEAT and Polygon engineers both put it bluntly: the current Blast is onlyEthereumIt is just a Deposit contract that receives recharges. This contract can be upgraded under the control of 3/5 multi-signatures. In other words, the code logic of the contract may be rewritten, and you can still rug it if you want. At the same time, Blast only claims to implement the Rollup structure, but now it is just an empty shell, and even the withdrawal function will not be launched until February next year.
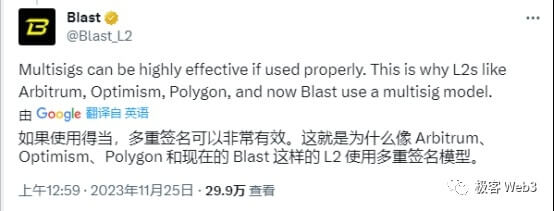
 And Blast can't bear to show weakness. Most Rollups rely on a set of multi-signature management contracts to upgrade their permissions. Other Layer2 companies accuse "Blast of using multi-signature" and they are just laughing at the fifty steps and the hundred steps.
And Blast can't bear to show weakness. Most Rollups rely on a set of multi-signature management contracts to upgrade their permissions. Other Layer2 companies accuse "Blast of using multi-signature" and they are just laughing at the fifty steps and the hundred steps.
Layer2 multi-signature is a long-standing problem
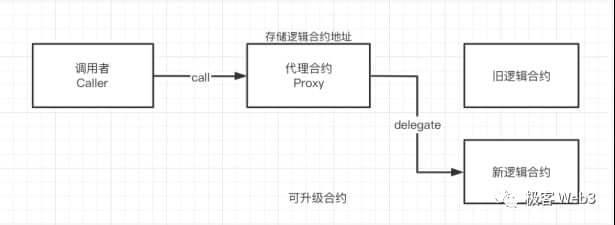
In fact, multi-signing of Layer 2 contracts is a long-standing problem. As early as July this year, L7BEAT conducted a special survey on the upgradability of the Rollup contract. The so-called "upgradeability" means changing the logical contract address pointed by the agent contract to achieve the effect of changing the contract logic. If the changed new contract contains malicious logic, Layer2 officials can remove the user资产stolen.
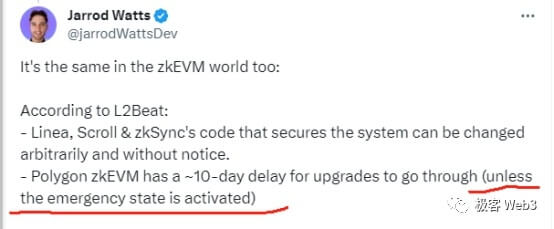
According to L2BEAT data, current mainstream rollups such as Arbitrum, Optimism, Loopring, ZKSync Lite, ZkSync Era, Starknet, Polygon ZKEVM, etc. all use multi-signature authorized upgradeable contracts, which can bypass time lock restrictions and upgrade immediately. (You can read Geek web3’s previous articles: The Game of Credit: Rollups Controlled by Multi-Signature and Committees)
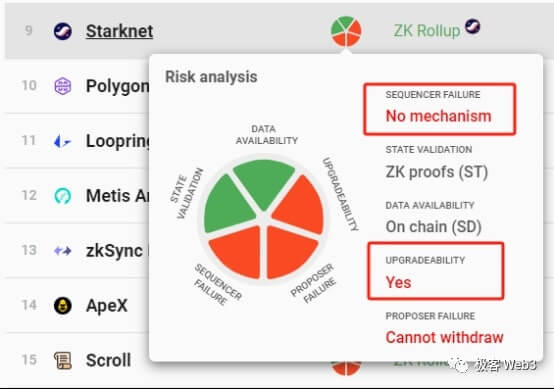
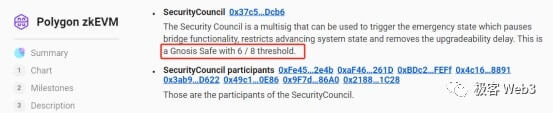
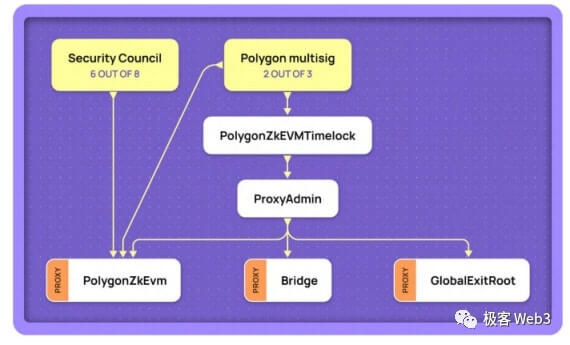
 What is surprising is that Optimism used to only use an EOA address to manage contract upgrades, and even multi-signature was only added in October this year. As for Polygon zkEVM, which has criticized Blast, it can also conduct an "emergency takeover" of the Rollup contract under the 10/6 multi-signature authorization, transforming Layer 8 from contract governance to "naked human governance." Interestingly, the Polygon engineer who criticized Blast above also mentioned this, but was vague.
What is surprising is that Optimism used to only use an EOA address to manage contract upgrades, and even multi-signature was only added in October this year. As for Polygon zkEVM, which has criticized Blast, it can also conduct an "emergency takeover" of the Rollup contract under the 10/6 multi-signature authorization, transforming Layer 8 from contract governance to "naked human governance." Interestingly, the Polygon engineer who criticized Blast above also mentioned this, but was vague.
 So what is the significance of this "emergency mode"? Why do most Rollups leave themselves a panic button or backdoor? according to Vitalik According to previous statements, Rollup needs to frequently update the contracts deployed on ETH during the iteration process. Without the introduction of upgradeable means such as proxy contracts, it will be difficult to iterate efficiently.
So what is the significance of this "emergency mode"? Why do most Rollups leave themselves a panic button or backdoor? according to Vitalik According to previous statements, Rollup needs to frequently update the contracts deployed on ETH during the iteration process. Without the introduction of upgradeable means such as proxy contracts, it will be difficult to iterate efficiently.
In addition, hosting a large number of资产Smart contracts may have subtle bugs, and the Layer2 development team is inevitably negligent. If certain vulnerabilities are exploited by hackers, it may lead to a large number of资产Stolen. So, Layer2 is also good,DeFi Regardless of the agreement, there is often an emergency button set up, and "committee members" can intervene when necessary to prevent certain vicious incidents from happening.
 Of course, the committee set up by Layer 2 can often bypass time lock restrictions and immediately upgrade the contract code. From a certain perspective, they seem to be more taboo than external factors such as hackers. Or, in any case, hosting a huge amount of资产It is difficult for all smart contracts to avoid a certain degree of "trust assumption", that is, it is assumed that the multi-signature controller behind the contract does not do evil. Unless the contract is designed to be non-upgradeable and there is no threat to users资产Security bug.
Of course, the committee set up by Layer 2 can often bypass time lock restrictions and immediately upgrade the contract code. From a certain perspective, they seem to be more taboo than external factors such as hackers. Or, in any case, hosting a huge amount of资产It is difficult for all smart contracts to avoid a certain degree of "trust assumption", that is, it is assumed that the multi-signature controller behind the contract does not do evil. Unless the contract is designed to be non-upgradeable and there is no threat to users资产Security bug.
The reality is that the current mainstream Layer2 either allows its own committee to update the contract immediately, or introduces a relatively short time lock limit (for example, anyone who wants to upgrade dYdX contract, there is a delay of at least 48 hours). If people find out that the committee intends to mix stolen content into the new version of the contract code,资产Based on the malicious logic, users theoretically have enough reaction time to urgently withdraw their assets from Layer 1.
(For information about forced withdrawal and escape cabin functions, you can read our previous article "How important are forced withdrawal and escape cabin functions to Layer2?"
 (Time lock allows you to perform certain operations after a delay)
(Time lock allows you to perform certain operations after a delay)
But the crux of the matter is that many Layer 2 companies can bypass Sequencer SortThe forced withdrawal function of the server is not set up. If the official Layer2 wants to do something evil, it can first letSortThe server rejects everyone's withdrawal request, and then transfers the user's assets to the L2 account controlled by Layer2 officials. After that, the official will update the Rollup contract according to their own needs. After the time lock delay is over, all user assets can be transferred to the ETH chain.
Of course, the actual situation may be worse than what I said, because most Rollup officials can upgrade contracts without time lock restrictions, which means that rugs worth hundreds of millions of dollars can be completed almost instantly.
A truly trustless Layer 2 should make the contract upgrade delay greater than the forced withdrawal delay.
In fact, to solve Layer2 trustlessness/security issues, the following things need to be done:
Set up a censorship-resistant withdrawal exit on Layer1 so that users canSortWith the server permission, assets can be directly transferred from Layer 2 to the ETH chain. The delay in forced withdrawal should not be too long, so as to ensure that user assets can be withdrawn from L2 quickly;
Anyone who wants to upgrade the Layer 2 contract must be subject to the time lock delay limit, and the contract upgrade should take effect later than the mandatory withdrawal. For example, the contract upgrade of dYdX now has a delay of at least 48 hours, so the delay in taking effect of the forced withdrawal/escape hatch mode should be reduced to within 48 hours. In this way, after users discover that the dYdX project team wants to incorporate malicious code into the new version of the contract, they can withdraw assets from Layer 2 to Layer 1 before the contract is updated.
Currently, the vast majority of Rollups that have launched forced withdrawal/escape cabin mechanisms do not meet the above conditions. For example, dYdX’s forced withdrawal/escape hatch has a maximum delay of 7 days, but the dYdX committee’s contract upgrade delay is only 48 hours. In other words, the committee can complete the deployment of the new contract before the user’s forced withdrawal takes effect. Steal assets before the user escapes.
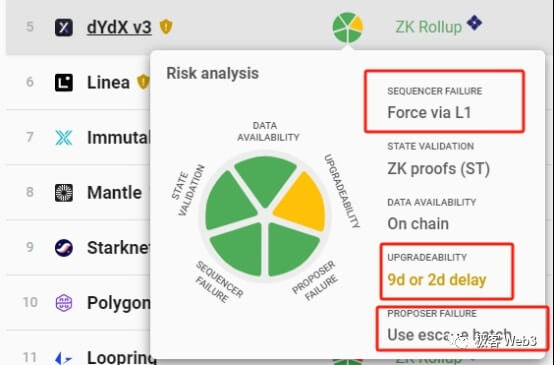 From this perspective, except for Fuel, ZKSpace, and Degate, other rollups cannot guarantee that users’ forced withdrawals will be processed before the contract upgrade, and there is a high degree of trust assumption.
From this perspective, except for Fuel, ZKSpace, and Degate, other rollups cannot guarantee that users’ forced withdrawals will be processed before the contract upgrade, and there is a high degree of trust assumption.
 Many use Validium solutions (DA inEthereumAlthough off-chain implementation) projects have long contract upgrade delays (such as 8 days or more), Validium often relies on off-chain DAC nodes to publish the latest data, and DAC may launch data withholding attacks, making the forced withdrawal function Invalid, so it does not comply with the security model discussed above. (You can read our previous article "Firing Validium? Reunderstanding Layer2 from the perspective of the proposer of Danksharding")
Many use Validium solutions (DA inEthereumAlthough off-chain implementation) projects have long contract upgrade delays (such as 8 days or more), Validium often relies on off-chain DAC nodes to publish the latest data, and DAC may launch data withholding attacks, making the forced withdrawal function Invalid, so it does not comply with the security model discussed above. (You can read our previous article "Firing Validium? Reunderstanding Layer2 from the perspective of the proposer of Danksharding")
At this point, we seem to be able to draw a concise and clear conclusion: Layer 2 solutions other than Fuel, ZKSpace and DeGate are not trustless. Users either trust the Layer2 project party or the security committee set up by it not to do evil, or they trust the DAC nodes under the chain not to collude, or they trustSortThe server will not review your transaction (deny your request). There are currently only the above three Layer 2s that truly satisfy security, censorship resistance, and trustlessness.
Security is not only achieved by technology, but must also introduce social consensus
In fact, the topic we are talking about today is not new. The essence of Layer 2 pointed out in this article depends on the credibility of the project party, which has been pointed out by countless people. For example, Avalanche and Solana The founders have vigorously criticized this, but the problem is that these trust assumptions that exist on Layer 2 are not applicable to Layer 1 and even allBlockchainThe same exists on the project.
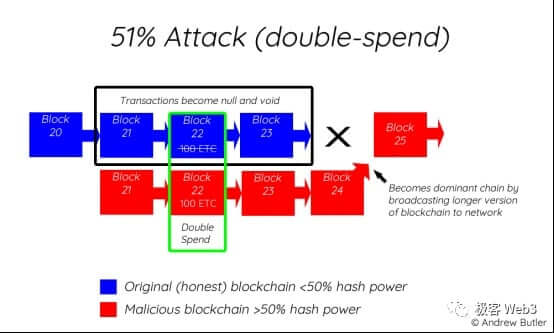
For example, we need to assume Solana The Validator nodes that account for 2/3 of the pledge weight in the network do not collude. It needs to be assumed that they account forBitcoinThe top two mining pools, which hold the majority of the computing power share, do not unite to launch a 51% attack to roll back the longest chain. Although these assumptions are difficult to break, "difficult" does not mean "impossible."
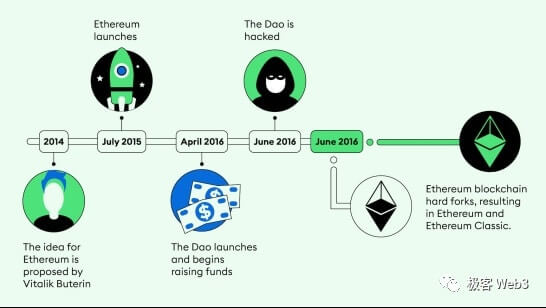
Once an evil act occurs in a traditional Layer 1 public chain that causes a large number of user assets to be damaged, the problematic chain will often be abandoned and a new chain will be forked through social consensus (refer to The 2016 The DAO events leading toEthereumForked into ETH and ETC). If someone attempts a malicious fork, everyone must choose which "more reliable" fork to follow through social consensus. (For example, most people do not follow the ETHW project)
 Social consensus is the guaranteeBlockchainThe project and even the items it carries DeFi The root of the orderly operation of the protocol is that even error correction mechanisms such as contract code audits and community members disclosing problems with a project are part of social consensus. And it is achieved purely by technology.Decentralization, often cannot play the greatest role, and often remain at the theoretical level.
Social consensus is the guaranteeBlockchainThe project and even the items it carries DeFi The root of the orderly operation of the protocol is that even error correction mechanisms such as contract code audits and community members disclosing problems with a project are part of social consensus. And it is achieved purely by technology.Decentralization, often cannot play the greatest role, and often remain at the theoretical level.
What really comes into play at critical moments is often social consensus that has nothing to do with technology, public opinion supervision that has nothing to do with academic papers, and mass recognition that has nothing to do with technical narratives.
We can imagine the following scenario: a POW public chain that only a few hundred people have heard of is temporarily at a high levelDecentralizationstate, because there has not yet been a situation where one company is dominant. But if a mining company suddenly invests all its computing power into the POW chain, its own computing power will be many times higher than that of all other miners. At this time, the computing power of this POW chainDecentralizationwill be disintegrated instantly. If the mining company intends to do evil, people can only correct the mistake through social consensus.
 On the other hand, the so-called Layer 2, no matter how sophisticated its mechanism design is, cannot avoid the link of social consensus. Even L2 such as Fuel, DeGate and ZKSpace, where officials can hardly do evil, the Layer 1- EthereumIt is also highly dependent on social consensus/community-public opinion supervision.
On the other hand, the so-called Layer 2, no matter how sophisticated its mechanism design is, cannot avoid the link of social consensus. Even L2 such as Fuel, DeGate and ZKSpace, where officials can hardly do evil, the Layer 1- EthereumIt is also highly dependent on social consensus/community-public opinion supervision.
What's more, we believe that the contract cannot be upgraded because we listened to the submissions of the contract audit agency and L2BEAT, but these agencies may be negligent or lie. Although this probability is extremely low, we have to admit that a small assumption of trust is still introduced.
However, the open-source data nature of the blockchain itself allows anyone, including hackers, to check whether the contract contains malicious logic. In fact, the trust assumption has been minimized, which greatly reduces the cost of social consensus. If this cost is reduced to a low enough level, we can default to "trustlessness".
 Of course, except for the three mentioned above, other Layer 2s have no so-called trust at all. What truly guarantees security at critical moments is still social consensus. The technical component is often just to facilitate people to carry out social consensus supervision. If the technology of a project is superior, but it is not widely recognized and cannot attract a large community group, then itsDecentralizationGovernance and social consensus itself are also difficult to effectively develop.
Of course, except for the three mentioned above, other Layer 2s have no so-called trust at all. What truly guarantees security at critical moments is still social consensus. The technical component is often just to facilitate people to carry out social consensus supervision. If the technology of a project is superior, but it is not widely recognized and cannot attract a large community group, then itsDecentralizationGovernance and social consensus itself are also difficult to effectively develop.
Technology is indeed important, but more often than not, whether it can be widely recognized and whether it can develop a strong community culture are factors that are more important, more valuable, and more conducive to project development than technology.
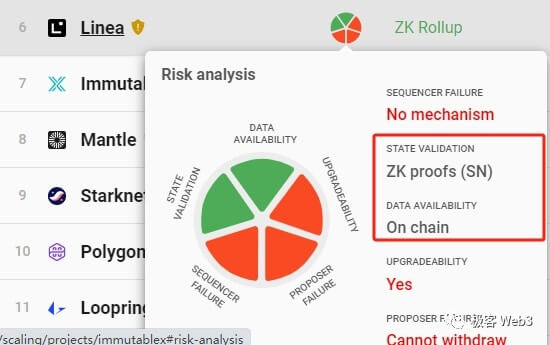
We might as well take zkRollup as an example. Currently, many zkRollups only implement the validity certification system and DA data on-chain. It can externally prove that the user transactions it handles and all transfers made are valid. NotSortThe device is forged, and there is no evil in the matter of "state transition", but Layer2 official orSortThis is not the only scenario where weapons do evil.
We can approximate that the ZK proof system essentially only greatly reduces the cost of people's supervision of Layer 2, but there are many things that cannot be solved by technology itself and must rely on the intervention of human rule or social consensus.
 If L2 officials do not set up anti-censorship exits such as forced withdrawals, or if the officials try to upgrade the contract and incorporate logic that can steal user assets, community members will have to rely on social consensus and public opinion fermentation to correct errors. At this moment, whether technology is superior or not no longer seems to be the most important. Rather than saying that technology is important for security, it is more important to say that the mechanism design itself that facilitates people to develop social consensus is more important. This In fact, this is the true meaning of Layer 2 and even blockchain.
If L2 officials do not set up anti-censorship exits such as forced withdrawals, or if the officials try to upgrade the contract and incorporate logic that can steal user assets, community members will have to rely on social consensus and public opinion fermentation to correct errors. At this moment, whether technology is superior or not no longer seems to be the most important. Rather than saying that technology is important for security, it is more important to say that the mechanism design itself that facilitates people to develop social consensus is more important. This In fact, this is the true meaning of Layer 2 and even blockchain.
From the perspective of Blast, which relies purely on social consensus for supervision, we should look at the relationship between social consensus and technical implementation more directly, rather than simply based on "which L2 is closer to the Layer 2 in Vitalik's mouth than the other L2" Determine the merits of a project. When a project has gained recognition and attention from millions of people, social consensus has been formed.MarketingIt doesn’t matter whether you rely on technical narrative or not, because the result itself is more important than the process.
It is true that social consensus itself is an extension of democratic politics;real worldThe shortcomings of democratic governance have been proven, but the open source and data transparency of the blockchain itself have greatly reduced the cost of social consensus. Therefore,Web3 There is an essential difference between the "rule of man" in China and the "rule of man" in actual sovereign states.
If we regard the blockchain itself as a technical means to improve information transparency issues in democratic governance, rather than simply pursuing "Trustless achieved purely by code" that is always out of reach, everything seems to become much more optimistic and clear. Only by getting rid of the arrogance and prejudice inherent in the technical elite and embracing a broaderswipe.Ethereum Only the Layer2 system can truly become a world-class mass adoption金融infrastructure.